Problem
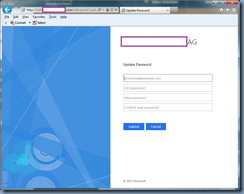
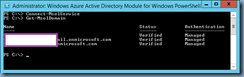
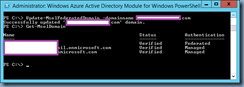
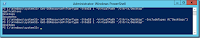
You’ve used the Connect-MsolService cmdlet to connect to the WAAD instance then attempt to execute the Set-MsolADFSContext -computer <ADFSserver>.tokiomillennium.com command to hook into the local ADFS server but notice that you get the password prompt that doesn’t appear to accept any passwords that you attempt to use:
![image image]()
After the second attempt to authenticate, you are presented with the following error:
PS C:\> Set-MsolADFSContext -computer adfs.domain.com
Set-MsolADFSContext : The connection to adfs.domain.com Active Directo
ry Federation Services 2.0 server failed due to invalid credentials.
At line:1 char:20
+ Set-MsolADFSContext <<<< -computer adfs.domain.com
+ CategoryInfo : InvalidOperation: (:) [Set-MsolADFSContext], Fed
erationException
+ FullyQualifiedErrorId : ConnectionToGenevaServerFailed,Microsoft.Online.
Identity.Federation.Powershell.ContextCredentialsCommand
PS C:\>
![image image]()
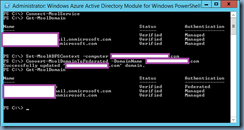
You’ve ensured that Enable-PSRemoting -force has been executed successfully as outlined in the following KB: https://support.microsoft.com/en-us/kb/2587730
![image image]()
You’ve also confirmed that the port 5985 is opened on the firewall as per the following TechNet blog: http://blogs.technet.com/b/tune_in_to_windows_intune/archive/2013/11/07/the-connection-to-adfs-domain-com-active-directory-federation-services-2-0-server-failed-due-to-invalid-credentials.aspx
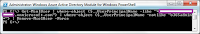
You proceed to use the Set-MsolADFSContext cmdlet with the -logfile c:\log.txt switch for more information:
![image image]()
… and obtain the following information:
11/16/2015 10:07:37 AM Command Set-MsolADFSContext invoked.
11/16/2015 10:07:37 AM Creating ADFS Server PS session.
11/16/2015 10:07:37 AM ContextCredentialsCommand:CreatePowerShellSessionToGenevaServer: Invoked.
11/16/2015 10:07:37 AM Creating PS session to 'adfs.domain.com' ADFS server
11/16/2015 10:07:37 AM Connect using current logged-on user creds.
11/16/2015 10:07:37 AM Runspace Connection info: Scheme:http Port:5985, AuthenticationType:Default Uri:adfs.domain.com AppName:wsman, Shell:http://schemas.microsoft.com/powershell/Microsoft.PowerShell
11/16/2015 10:07:37 AM Connection Uri: http://adfs.domain.com:5985/wsman/
11/16/2015 10:07:38 AM Opening runspace to 'http://adfs.domain.com:5985/wsman/'
11/16/2015 10:07:38 AM System.Management.Automation.Remoting.PSRemotingTransportException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at System.Management.Automation.Runspaces.Internal.RunspacePoolInternal.EndOpen(IAsyncResult asyncResult)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
11/16/2015 10:07:38 AM fullyQualifiedErrorId: System.Management.Automation.Remoting.PSRemotingDataStructureException
11/16/2015 10:07:38 AM Command failed: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.ParseAndThrowErrorRecord(ErrorRecord errorRecord, String overRideErrorId)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.OpenToGenevaServer(PSCredential serverCredential)
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.<>c__DisplayClass2.<CreatePowerShellSessionToGenevaServer>b__0()
at Microsoft.Online.Identity.Federation.Powershell.Utility.InvokeOperationWithRetry(Action operation, Type exceptionType, String errorId, Int32 retryCount, Int32 retryWaitTimeInMilliseconds)
11/16/2015 10:07:38 AM Retry errorId: ConnectionToGenevaServerFailed
11/16/2015 10:07:38 AM Retry exception: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException
11/16/2015 10:07:38 AM Going to sleep mode for 1000 milliseconds before reattempt - 2
11/16/2015 10:07:39 AM Runspace Connection info: Scheme:http Port:5985, AuthenticationType:Default Uri:adfs.domain.com AppName:wsman, Shell:http://schemas.microsoft.com/powershell/Microsoft.PowerShell
11/16/2015 10:07:39 AM Connection Uri: http://adfs.domain.com:5985/wsman/
11/16/2015 10:07:39 AM Opening runspace to 'http://adfs.domain.com:5985/wsman/'
11/16/2015 10:07:39 AM System.Management.Automation.Remoting.PSRemotingTransportException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at System.Management.Automation.Runspaces.Internal.RunspacePoolInternal.EndOpen(IAsyncResult asyncResult)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
11/16/2015 10:07:39 AM fullyQualifiedErrorId: System.Management.Automation.Remoting.PSRemotingDataStructureException
11/16/2015 10:07:39 AM Command failed: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.ParseAndThrowErrorRecord(ErrorRecord errorRecord, String overRideErrorId)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.OpenToGenevaServer(PSCredential serverCredential)
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.<>c__DisplayClass2.<CreatePowerShellSessionToGenevaServer>b__0()
at Microsoft.Online.Identity.Federation.Powershell.Utility.InvokeOperationWithRetry(Action operation, Type exceptionType, String errorId, Int32 retryCount, Int32 retryWaitTimeInMilliseconds)
11/16/2015 10:07:39 AM Retry errorId: ConnectionToGenevaServerFailed
11/16/2015 10:07:39 AM Retry exception: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException
11/16/2015 10:07:39 AM Going to sleep mode for 2000 milliseconds before reattempt - 3
11/16/2015 10:07:41 AM Runspace Connection info: Scheme:http Port:5985, AuthenticationType:Default Uri:adfs.domain.com AppName:wsman, Shell:http://schemas.microsoft.com/powershell/Microsoft.PowerShell
11/16/2015 10:07:41 AM Connection Uri: http://adfs.domain.com:5985/wsman/
11/16/2015 10:07:41 AM Opening runspace to 'http://adfs.domain.com:5985/wsman/'
11/16/2015 10:07:41 AM System.Management.Automation.Remoting.PSRemotingTransportException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at System.Management.Automation.Runspaces.Internal.RunspacePoolInternal.EndOpen(IAsyncResult asyncResult)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
11/16/2015 10:07:41 AM fullyQualifiedErrorId: System.Management.Automation.Remoting.PSRemotingDataStructureException
11/16/2015 10:07:41 AM Command failed: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.ParseAndThrowErrorRecord(ErrorRecord errorRecord, String overRideErrorId)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.OpenToGenevaServer(PSCredential serverCredential)
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.<>c__DisplayClass2.<CreatePowerShellSessionToGenevaServer>b__0()
at Microsoft.Online.Identity.Federation.Powershell.Utility.InvokeOperationWithRetry(Action operation, Type exceptionType, String errorId, Int32 retryCount, Int32 retryWaitTimeInMilliseconds)
11/16/2015 10:07:41 AM Retry errorId: ConnectionToGenevaServerFailed
11/16/2015 10:07:41 AM Retry exception: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException
11/16/2015 10:07:41 AM Failure after too many retry attempts...
11/16/2015 10:07:41 AM Wrong credentials to ADFS Server connection, attempt #'1'
11/16/2015 10:07:41 AM Prompting the user for 'adfs.domain.com' ADFS Server creds.
11/16/2015 10:07:41 AM ContextCredentialsCommand:GetServerCredentials: Invoked.
11/16/2015 10:08:04 AM Runspace Connection info: Scheme:http Port:5985, AuthenticationType:Default Uri:adfs.domain.com AppName:wsman, Shell:http://schemas.microsoft.com/powershell/Microsoft.PowerShell
11/16/2015 10:08:04 AM Connection Uri: http://adfs.domain.com:5985/wsman/
11/16/2015 10:08:04 AM Opening runspace to 'http://adfs.domain.com:5985/wsman/'
11/16/2015 10:08:04 AM System.Management.Automation.Remoting.PSRemotingTransportException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at System.Management.Automation.Runspaces.Internal.RunspacePoolInternal.EndOpen(IAsyncResult asyncResult)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
11/16/2015 10:08:04 AM fullyQualifiedErrorId: System.Management.Automation.Remoting.PSRemotingDataStructureException
11/16/2015 10:08:04 AM Command failed: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.ParseAndThrowErrorRecord(ErrorRecord errorRecord, String overRideErrorId)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.OpenToGenevaServer(PSCredential serverCredential)
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.<>c__DisplayClass2.<CreatePowerShellSessionToGenevaServer>b__0()
at Microsoft.Online.Identity.Federation.Powershell.Utility.InvokeOperationWithRetry(Action operation, Type exceptionType, String errorId, Int32 retryCount, Int32 retryWaitTimeInMilliseconds)
11/16/2015 10:08:04 AM Retry errorId: ConnectionToGenevaServerFailed
11/16/2015 10:08:04 AM Retry exception: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException
11/16/2015 10:08:04 AM Going to sleep mode for 1000 milliseconds before reattempt - 2
11/16/2015 10:08:05 AM Runspace Connection info: Scheme:http Port:5985, AuthenticationType:Default Uri:adfs.domain.com AppName:wsman, Shell:http://schemas.microsoft.com/powershell/Microsoft.PowerShell
11/16/2015 10:08:05 AM Connection Uri: http://adfs.domain.com:5985/wsman/
11/16/2015 10:08:06 AM Opening runspace to 'http://adfs.domain.com:5985/wsman/'
11/16/2015 10:08:06 AM System.Management.Automation.Remoting.PSRemotingTransportException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at System.Management.Automation.Runspaces.Internal.RunspacePoolInternal.EndOpen(IAsyncResult asyncResult)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
11/16/2015 10:08:06 AM fullyQualifiedErrorId: System.Management.Automation.Remoting.PSRemotingDataStructureException
11/16/2015 10:08:06 AM Command failed: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.ParseAndThrowErrorRecord(ErrorRecord errorRecord, String overRideErrorId)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.OpenToGenevaServer(PSCredential serverCredential)
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.<>c__DisplayClass2.<CreatePowerShellSessionToGenevaServer>b__0()
at Microsoft.Online.Identity.Federation.Powershell.Utility.InvokeOperationWithRetry(Action operation, Type exceptionType, String errorId, Int32 retryCount, Int32 retryWaitTimeInMilliseconds)
11/16/2015 10:08:06 AM Retry errorId: ConnectionToGenevaServerFailed
11/16/2015 10:08:06 AM Retry exception: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException
11/16/2015 10:08:06 AM Going to sleep mode for 2000 milliseconds before reattempt - 3
11/16/2015 10:08:08 AM Runspace Connection info: Scheme:http Port:5985, AuthenticationType:Default Uri:adfs.domain.com AppName:wsman, Shell:http://schemas.microsoft.com/powershell/Microsoft.PowerShell
11/16/2015 10:08:08 AM Connection Uri: http://adfs.domain.com:5985/wsman/
11/16/2015 10:08:08 AM Opening runspace to 'http://adfs.domain.com:5985/wsman/'
11/16/2015 10:08:08 AM System.Management.Automation.Remoting.PSRemotingTransportException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at System.Management.Automation.Runspaces.Internal.RunspacePoolInternal.EndOpen(IAsyncResult asyncResult)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
11/16/2015 10:08:08 AM fullyQualifiedErrorId: System.Management.Automation.Remoting.PSRemotingDataStructureException
11/16/2015 10:08:08 AM Command failed: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.ParseAndThrowErrorRecord(ErrorRecord errorRecord, String overRideErrorId)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.OpenToGenevaServer(PSCredential serverCredential)
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.<>c__DisplayClass2.<CreatePowerShellSessionToGenevaServer>b__0()
at Microsoft.Online.Identity.Federation.Powershell.Utility.InvokeOperationWithRetry(Action operation, Type exceptionType, String errorId, Int32 retryCount, Int32 retryWaitTimeInMilliseconds)
11/16/2015 10:08:08 AM Retry errorId: ConnectionToGenevaServerFailed
11/16/2015 10:08:08 AM Retry exception: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException
11/16/2015 10:08:08 AM Failure after too many retry attempts...
11/16/2015 10:08:08 AM Wrong credentials to ADFS Server connection, attempt #'2'
11/16/2015 10:08:08 AM Prompting the user for 'adfs.domain.com' ADFS Server creds.
11/16/2015 10:08:08 AM ContextCredentialsCommand:GetServerCredentials: Invoked.
11/16/2015 10:08:22 AM Runspace Connection info: Scheme:http Port:5985, AuthenticationType:Default Uri:adfs.domain.com AppName:wsman, Shell:http://schemas.microsoft.com/powershell/Microsoft.PowerShell
11/16/2015 10:08:22 AM Connection Uri: http://adfs.domain.com:5985/wsman/
11/16/2015 10:08:23 AM Opening runspace to 'http://adfs.domain.com:5985/wsman/'
11/16/2015 10:08:23 AM System.Management.Automation.Remoting.PSRemotingTransportException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at System.Management.Automation.Runspaces.Internal.RunspacePoolInternal.EndOpen(IAsyncResult asyncResult)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
11/16/2015 10:08:23 AM fullyQualifiedErrorId: System.Management.Automation.Remoting.PSRemotingDataStructureException
11/16/2015 10:08:23 AM Command failed: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.ParseAndThrowErrorRecord(ErrorRecord errorRecord, String overRideErrorId)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.OpenToGenevaServer(PSCredential serverCredential)
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.<>c__DisplayClass2.<CreatePowerShellSessionToGenevaServer>b__0()
at Microsoft.Online.Identity.Federation.Powershell.Utility.InvokeOperationWithRetry(Action operation, Type exceptionType, String errorId, Int32 retryCount, Int32 retryWaitTimeInMilliseconds)
11/16/2015 10:08:23 AM Retry errorId: ConnectionToGenevaServerFailed
11/16/2015 10:08:23 AM Retry exception: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException
11/16/2015 10:08:23 AM Going to sleep mode for 1000 milliseconds before reattempt - 2
11/16/2015 10:08:24 AM Runspace Connection info: Scheme:http Port:5985, AuthenticationType:Default Uri:adfs.domain.com AppName:wsman, Shell:http://schemas.microsoft.com/powershell/Microsoft.PowerShell
11/16/2015 10:08:24 AM Connection Uri: http://adfs.domain.com:5985/wsman/
11/16/2015 10:08:24 AM Opening runspace to 'http://adfs.domain.com:5985/wsman/'
11/16/2015 10:08:24 AM System.Management.Automation.Remoting.PSRemotingTransportException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at System.Management.Automation.Runspaces.Internal.RunspacePoolInternal.EndOpen(IAsyncResult asyncResult)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
11/16/2015 10:08:24 AM fullyQualifiedErrorId: System.Management.Automation.Remoting.PSRemotingDataStructureException
11/16/2015 10:08:24 AM Command failed: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.ParseAndThrowErrorRecord(ErrorRecord errorRecord, String overRideErrorId)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.OpenToGenevaServer(PSCredential serverCredential)
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.<>c__DisplayClass2.<CreatePowerShellSessionToGenevaServer>b__0()
at Microsoft.Online.Identity.Federation.Powershell.Utility.InvokeOperationWithRetry(Action operation, Type exceptionType, String errorId, Int32 retryCount, Int32 retryWaitTimeInMilliseconds)
11/16/2015 10:08:24 AM Retry errorId: ConnectionToGenevaServerFailed
11/16/2015 10:08:24 AM Retry exception: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException
11/16/2015 10:08:24 AM Going to sleep mode for 2000 milliseconds before reattempt - 3
11/16/2015 10:08:26 AM Runspace Connection info: Scheme:http Port:5985, AuthenticationType:Default Uri:adfs.domain.com AppName:wsman, Shell:http://schemas.microsoft.com/powershell/Microsoft.PowerShell
11/16/2015 10:08:26 AM Connection Uri: http://adfs.domain.com:5985/wsman/
11/16/2015 10:08:26 AM Opening runspace to 'http://adfs.domain.com:5985/wsman/'
11/16/2015 10:08:26 AM System.Management.Automation.Remoting.PSRemotingTransportException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at System.Management.Automation.Runspaces.Internal.RunspacePoolInternal.EndOpen(IAsyncResult asyncResult)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
11/16/2015 10:08:26 AM fullyQualifiedErrorId: System.Management.Automation.Remoting.PSRemotingDataStructureException
11/16/2015 10:08:26 AM Command failed: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException: Connecting to remote server adfs.domain.com failed with the following error message : WinRM cannot process the request. The following error with errorcode 0x80090322 occurred while using Kerberos authentication: An unknown security error occurred.
Possible causes are:
-The user name or password specified are invalid.
-Kerberos is used when no authentication method and no user name are specified.
-Kerberos accepts domain user names, but not local user names.
-The Service Principal Name (SPN) for the remote computer name and port does not exist.
-The client and remote computers are in different domains and there is no trust between the two domains.
After checking for the above issues, try the following:
-Check the Event Viewer for events related to authentication.
-Change the authentication method; add the destination computer to the WinRM TrustedHosts configuration setting or use HTTPS transport.
Note that computers in the TrustedHosts list might not be authenticated.
-For more information about WinRM configuration, run the following command: winrm help config. For more information, see the about_Remote_Troubleshooting Help topic.
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.ParseAndThrowErrorRecord(ErrorRecord errorRecord, String overRideErrorId)
at Microsoft.Online.Identity.Federation.Powershell.PowerShellSession.VerifyAndReconnectRunSpacePool()
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.OpenToGenevaServer(PSCredential serverCredential)
at Microsoft.Online.Identity.Federation.Powershell.ContextCredentialsCommand.<>c__DisplayClass2.<CreatePowerShellSessionToGenevaServer>b__0()
at Microsoft.Online.Identity.Federation.Powershell.Utility.InvokeOperationWithRetry(Action operation, Type exceptionType, String errorId, Int32 retryCount, Int32 retryWaitTimeInMilliseconds)
11/16/2015 10:08:26 AM Retry errorId: ConnectionToGenevaServerFailed
11/16/2015 10:08:26 AM Retry exception: Microsoft.Online.Identity.Federation.Powershell.IdentityFederationException
11/16/2015 10:08:26 AM Failure after too many retry attempts...
11/16/2015 10:08:26 AM Wrong credentials to ADFS Server connection, attempt #'3'
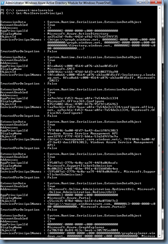
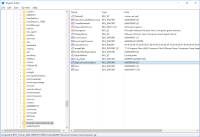
Reviewing the event logs of the ADFS server (not the proxy) show that the following Event ID 4 error is logged:
The Kerberos client received a KRB_AP_ERR_MODIFIED error from the server bmadfs01$. The target name used was HTTP/adfs.domain.com. This indicates that the target server failed to decrypt the ticket provided by the client. This can occur when the target server principal name (SPN) is registered on an account other than the account the target service is using. Ensure that the target SPN is only registered on the account used by the server. This error can also happen if the target service account password is different than what is configured on the Kerberos Key Distribution Center for that target service. Ensure that the service on the server and the KDC are both configured to use the same password. If the server name is not fully qualified, and the target domain (domain.COM) is different from the client domain (domain.COM), check if there are identically named server accounts in these two domains, or use the fully-qualified name to identify the server.
Log Name: System
Source: Security-Kerberos
Event ID: 4
Level: Error
![image image]()
You’ve reviewed the following forum post and your environment does not exhibit the SPN issue:
https://social.technet.microsoft.com/Forums/windows/en-US/a4c5c787-ea65-4150-8d16-2a19c569a589/enterpssession-winrm-cannot-process-the-request-kerberos-authentication-error-0x80090322?forum=winserverpowershell
Solution
The solution to this issue if none of the above troubleshooting suggestions apply to your environment actually to execute the Set-MsolADFSContext cmdlet using the internal ADFS server’s FQDN rather than the adfs A record you created to reference the server. The environment I worked in that exhibited this issue had an internal DNS A record adfs that mapped to the internal ADFS server so when the cmdlet was executed referencing this record, it caused the Kerberos error to be thrown and logged. As simple as this error could be, I find that this question gets asked quite often so I hope this blog post would help those encounter this issue.