Problem
You’ve just completed configuring a new Citrix XenDesktop site on your first delivery controller and proceed to install XenDesktop onto the second delivery controller then select the Scale your deployment – Connect this Deliver Controller to an existing Site to connect the second delivery controller to the site:
![image image]()
You proceed to specify the first delivery controller’s FQDN:
![image image]()
![image image]()
![image image]()
… but the process does not complete and displays the following message:
There was a problem communicating with the server
![image image]()
Clicking on the View details button displays the following:
Error Id: XDDS:CCA074AC
Exception:
Citrix.Console.Models.Exceptions.CommunicationErrorException There was a problem communicating with the server.
at Citrix.Console.PowerShellInteraction.CmdletExecutionMethods.CreateException[T](ICommonLog logger, ExecutionResults`1 results, ICmdletExecutionHost host)
at Citrix.Console.PowerShellInteraction.CmdletExecutionMethods.Execute[T](ISdkCmdlet`1 sdkCmd, ICmdletExecutionHost host, Boolean allowFailover)
at Citrix.Console.PowerShellInteraction.SdkServiceBase.GetDatabaseScript(ICmdletExecutionHost cmdletExecutionHost, String instanceAddress, SdkScriptType sdkScriptType, String serviceGroupName, String controllerSid, Boolean databaseIsLocal, String databaseName, DataStore dataStore)
at Citrix.Console.PowerShellSdk.DatabaseService.Scripts.GenerateSchemasScript.RunScript()
at Citrix.Console.PowerShellInteraction.PowerShellScript`1.Run()
at Citrix.Console.PowerShellSdk.DatabaseService.PSDatabaseService.AddControllerToDatabases(IEnumerable`1 databaseCredentials, String configServiceAddress, ScriptExecutionContext context, String controllerToAddAddress)
at Citrix.Console.PowerShellSdk.SiteService.Scripts.JoinExistingSiteScript.RunScript()
at Citrix.Console.PowerShellInteraction.PowerShellScript`1.Run()
at Citrix.Console.DeliveryCenter.UI.Dialogs.JoinExistingSiteDialogViewModel.OkBackgroundOperation(IProgressReporter progressReporter)
at Citrix.Console.Common.OperationTimer.TimeBlock(Action operation)
at Citrix.Console.CommonControls.ProgressDisplay.GenericProgressOperationWithFeedBack.PerformOperationInternal()
at Citrix.Console.CommonControls.ProgressDisplay.ProgressWindowOperation.PerformOperation()
at Citrix.Console.CommonControls.ProgressDisplay.ProgressWindowViewModel.PerformAction(Action operationComplete)
DesktopStudio_ErrorId : CommunicationError
Sdk Error Message : An invalid URL was given for the service. The value given was 'SVR-CTXDC-02.ccs.int'.
The reason given was: Failed to connect to back-end server 'SVR-CTXDC-02.ccs.int' on port 80 using binding WSHttp. The server may be off-line or may not be running the appropriate service
The HTTP service located at http://svr-ctxdc-02.ccs.int/Citrix/AdIdentityContract/v2 is unavailable. This could be because the service is too busy or because no endpoint was found listening at the specified address. Please ensure that the address is correct and try accessing the service again later.
The remote server returned an error: (503) Server Unavailable..
Sdk Error ID : Citrix.XDPowerShell.Status.CommunicationError,Citrix.ADIdentity.Sdk.DataStore.Commands.GetAcctDBSchemaCommand
ErrorCategory : ResourceUnavailable
DesktopStudio_PowerShellHistory : JoinExistingSiteScript
8/22/2016 9:44:04 PM
Get-ConfigDBConnection -AdminAddress "svr-ctxdc-01.ccs.int"
Get-AcctDBSchema -AdminAddress "SVR-CTXDC-02.ccs.int" -DatabaseName "CitrixBakery LaneSite" -ScriptType "Instance"
Get-AcctDBSchema : An invalid URL was given for the service. The value given was 'SVR-CTXDC-02.ccs.int'.
The reason given was: Failed to connect to back-end server 'SVR-CTXDC-02.ccs.int' on port 80 using binding WSHttp. The server may be off-line or may not be running the appropriate service
The HTTP service located at http://svr-ctxdc-02.ccs.int/Citrix/AdIdentityContract/v2 is unavailable. This could be because the service is too busy or because no endpoint was found listening at the specified address. Please ensure that the address is correct and try accessing the service again later.
The remote server returned an error: (503) Server Unavailable..
+ CategoryInfo : InvalidOperation: (:) [Get-AcctDBSchema], InvalidOperationException
+ FullyQualifiedErrorId : Citrix.XDPowerShell.Status.CommunicationError,Citrix.ADIdentity.Sdk.DataStore.Commands.GetAcctDBSchemaCommand
Inner Exception:
System.InvalidOperationException An invalid URL was given for the service. The value given was 'SVR-CTXDC-02.ccs.int'.
The reason given was: Failed to connect to back-end server 'SVR-CTXDC-02.ccs.int' on port 80 using binding WSHttp. The server may be off-line or may not be running the appropriate service
The HTTP service located at http://svr-ctxdc-02.ccs.int/Citrix/AdIdentityContract/v2 is unavailable. This could be because the service is too busy or because no endpoint was found listening at the specified address. Please ensure that the address is correct and try accessing the service again later.
The remote server returned an error: (503) Server Unavailable..
at System.Management.Automation.MshCommandRuntime.ThrowTerminatingError(ErrorRecord errorRecord)
Inner Exception:
System.ServiceModel.CommunicationException Failed to connect to back-end server 'SVR-CTXDC-02.ccs.int' on port 80 using binding WSHttp. The server may be off-line or may not be running the appropriate service
at Citrix.Fma.Sdk.CommonCmdlets.AdminConnection`1..ctor(ConnectionSpec connectionSpec)
at Citrix.Fma.Sdk.CommonCmdlets.AdminConnection`1.GetAdminConnection(String serverPortString, String endpointAddress, Nullable`1 binding)
at Citrix.Fma.Sdk.CommonCmdlets.CommonCmdletBase.CreateProxy(String adminAddress, String endpointAddress, Nullable`1 adminBinding)
at Citrix.Fma.Sdk.CommonCmdlets.WcfCmdletBase`1.OpenConnection(Boolean terminateOnFailure)
Inner Exception:
System.ServiceModel.ServerTooBusyException The HTTP service located at http://svr-ctxdc-02.ccs.int/Citrix/AdIdentityContract/v2 is unavailable. This could be because the service is too busy or because no endpoint was found listening at the specified address. Please ensure that the address is correct and try accessing the service again later.
Server stack trace:
at System.ServiceModel.Security.IssuanceTokenProviderBase`1.DoNegotiation(TimeSpan timeout)
at System.ServiceModel.Security.SspiNegotiationTokenProvider.OnOpen(TimeSpan timeout)
at System.ServiceModel.Security.WrapperSecurityCommunicationObject.OnOpen(TimeSpan timeout)
at System.ServiceModel.Channels.CommunicationObject.Open(TimeSpan timeout)
at System.ServiceModel.Security.CommunicationObjectSecurityTokenProvider.Open(TimeSpan timeout)
at System.ServiceModel.Security.SymmetricSecurityProtocol.OnOpen(TimeSpan timeout)
at System.ServiceModel.Security.WrapperSecurityCommunicationObject.OnOpen(TimeSpan timeout)
at System.ServiceModel.Channels.CommunicationObject.Open(TimeSpan timeout)
at System.ServiceModel.Channels.SecurityChannelFactory`1.ClientSecurityChannel`1.OnOpen(TimeSpan timeout)
at System.ServiceModel.Channels.CommunicationObject.Open(TimeSpan timeout)
at System.ServiceModel.Security.SecuritySessionSecurityTokenProvider.DoOperation(SecuritySessionOperation operation, EndpointAddress target, Uri via, SecurityToken currentToken, TimeSpan timeout)
at System.ServiceModel.Security.SecuritySessionSecurityTokenProvider.GetTokenCore(TimeSpan timeout)
at System.IdentityModel.Selectors.SecurityTokenProvider.GetToken(TimeSpan timeout)
at System.ServiceModel.Security.SecuritySessionClientSettings`1.ClientSecuritySessionChannel.OnOpen(TimeSpan timeout)
at System.ServiceModel.Channels.CommunicationObject.Open(TimeSpan timeout)
at System.ServiceModel.Channels.ServiceChannel.OnOpen(TimeSpan timeout)
at System.ServiceModel.Channels.CommunicationObject.Open(TimeSpan timeout)
Exception rethrown at [0]:
at System.Runtime.Remoting.Proxies.RealProxy.HandleReturnMessage(IMessage reqMsg, IMessage retMsg)
at System.Runtime.Remoting.Proxies.RealProxy.PrivateInvoke(MessageData& msgData, Int32 type)
at System.ServiceModel.ICommunicationObject.Open()
at Citrix.Fma.Sdk.CommonCmdlets.AdminConnection`1..ctor(ConnectionSpec connectionSpec)
Inner Exception:
System.Net.WebException The remote server returned an error: (503) Server Unavailable.
at System.Net.HttpWebRequest.GetResponse()
at System.ServiceModel.Channels.HttpChannelFactory`1.HttpRequestChannel.HttpChannelRequest.WaitForReply(TimeSpan timeout)
You notice the following error while parsing through the log output:
DesktopStudio_ErrorId : CommunicationError
Sdk Error Message : An invalid URL was given for the service. The value given was 'SVR-CTXDC-02.ccs.int'.
The reason given was: Failed to connect to back-end server 'SVR-CTXDC-02.ccs.int' on port 80 using binding WSHttp. The server may be off-line or may not be running the appropriate service
The HTTP service located at http://svr-ctxdc-02.ccs.int/Citrix/AdIdentityContract/v2 is unavailable. This could be because the service is too busy or because no endpoint was found listening at the specified address. Please ensure that the address is correct and try accessing the service again later.
The remote server returned an error: (503) Server Unavailable..
![image image]()
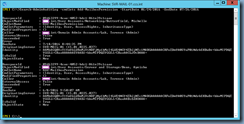
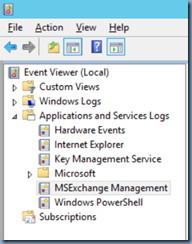
Solution
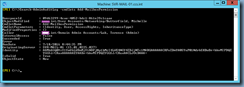
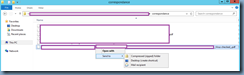
One of the reasons why this error would be thrown is if the following 2 services is not started:
- Citrix AD Identity Service
- Citrix App Library
![image image]()
![image image]()
Simply starting the 2 services and rerunning the Connect this Deliver Controller to an existing Site will allow you to connect the new delivery controller to the site.
![image image]()




















































![clip_image002[6] clip_image002[6]](http://lh3.googleusercontent.com/-ulAEq88C_78/V30Bo5e3r0I/AAAAAAAB9PQ/Kq3_0HCiggc/clip_image002%25255B6%25255D_thumb.jpg?imgmax=800)


























































![clip_image002[4] clip_image002[4]](http://lh3.googleusercontent.com/-I3PaqRmW_v4/WBsrB5sj8sI/AAAAAAAB9ps/o4gTZjXlebg/clip_image0024_thumb.jpg?imgmax=800)
![clip_image002[6] clip_image002[6]](http://lh3.googleusercontent.com/-hJYdAS7k0jA/WBsrEAxdwBI/AAAAAAAB9p0/7be-XRNDVmo/clip_image0026_thumb1.jpg?imgmax=800)
![clip_image002[8] clip_image002[8]](http://lh3.googleusercontent.com/-ThlhqwEZ00k/WBsrGrgcKJI/AAAAAAAB9p8/vkzEBKEugVg/clip_image0028_thumb1.jpg?imgmax=800)
![clip_image002[10] clip_image002[10]](http://lh3.googleusercontent.com/-IEUoeYGNg_Q/WBsrJAWiH5I/AAAAAAAB9qE/ql5u9Wi5m1Y/clip_image00210_thumb1.jpg?imgmax=800)
![clip_image002[12] clip_image002[12]](http://lh3.googleusercontent.com/-ruuFaY1VeBQ/WBsrLi13RWI/AAAAAAAB9qM/Y5nBu8xxj5Y/clip_image00212_thumb.jpg?imgmax=800)



![clip_image002[5] clip_image002[5]](http://lh3.googleusercontent.com/-NTCDWkRout8/WCOE2xLXdmI/AAAAAAAB9r4/ktKb-J1ZBPQ/clip_image002%25255B5%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
![clip_image002[7] clip_image002[7]](http://lh3.googleusercontent.com/-0utihaU-sB0/WCOE5kL8yLI/AAAAAAAB9sA/B-nwmvLszOE/clip_image002%25255B7%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
![clip_image002[9] clip_image002[9]](http://lh3.googleusercontent.com/-ds3lUkzml_c/WCOE7-vJZFI/AAAAAAAB9sI/OuUqHk1XfFs/clip_image002%25255B9%25255D_thumb%25255B1%25255D.jpg?imgmax=800)

![clip_image002[11] clip_image002[11]](http://lh3.googleusercontent.com/-SH__stZvexM/WCOFBstSmGI/AAAAAAAB9sY/M_qIwlbaLRg/clip_image002%25255B11%25255D_thumb%25255B1%25255D.jpg?imgmax=800)
![clip_image002[13] clip_image002[13]](http://lh3.googleusercontent.com/-J2OBMyi03IA/WCOFEpKn-eI/AAAAAAAB9sg/XCIsXImMGgs/clip_image002%25255B13%25255D_thumb%25255B1%25255D.jpg?imgmax=800)

